To protect against cyberattack, organization required to take multiple countermeasures.
Mentioned at the beginning that exploit techniques of cyberattack become more and more cunning and one of the traditional attack is “targeted e-mail attack”
Targeted e-mail attack is the specific attack to break net-work security of the organization by means of opening an attachment form an email which contained a virus. Upon determined the target, send emails in which titled credible for target and assumed as if it was an important notice then force receiver open the unauthorized attachment form.
This example shows that techniques of cyberattack is increasingly improved and sophisticated.
It is difficult to defend cyberattack completely with technical measures, therefore, take effective measures from multiple prospective is essential to against threats of cyberattack.
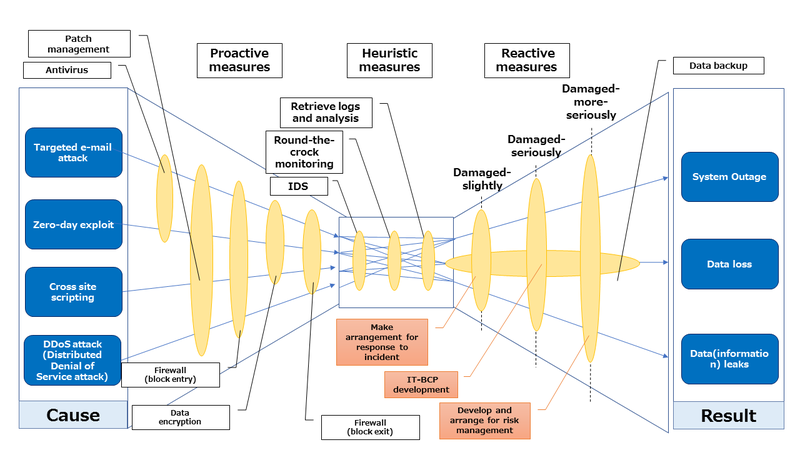
There are various types of measures against cyberattack will be found from multiple viewpoints.
As for defending current cyberattack, it is commonly said that taking an exit counter-measure (measure for communication from inside of the network to outside) is important than just only take entry counter-measure (measure for communication form the outside to inside of the network). Additionally, for example Bow-tie-Analysis is also effective approach to defend cyberattack. (refer to below figure). Taking this measure make possible to analyze the cause and result from the both side.